Creating a Governance Plan to Adhere to the NIST Cybersecurity Framework
Dan Timmer
|
Guest Contributor – Tom Neclerio, CISO & SVP of Security Services at SilverSky
In an increasingly digital world, cybersecurity has become a top priority for organizations of all sizes and industries. The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) provides a valuable set of guidelines and best practices to help organizations protect their information and assets. Creating a governance plan to adhere to the NIST CSF is crucial for building a robust cybersecurity posture. In this article, we will outline the steps to create such a plan and implement governance effectively.
Step 1: Understand the NIST CSF
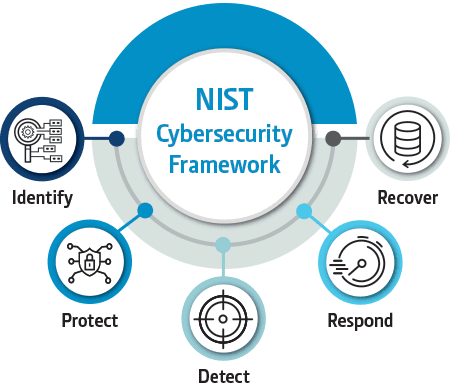
Before creating a governance plan, it’s essential to have a solid understanding of the NIST Cybersecurity Framework. The framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. Each function contains categories and subcategories that provide detailed guidance on cybersecurity practices. Start by thoroughly reviewing the NIST CSF documentation and identifying which components are relevant to your organization.
Step 2: Assess Your Current State
Once you are familiar with the NIST CSF, assess your organization’s current cybersecurity posture. Identify strengths and weaknesses, potential vulnerabilities, and areas where improvement is needed. This assessment should involve various stakeholders, including IT teams, security experts, and executives, to ensure a comprehensive understanding of the current state.
Step 3: Define Governance Roles and Responsibilities
Establish clear governance roles and responsibilities within your organization. Designate individuals or teams responsible for cybersecurity oversight, policy development, risk assessment, and incident response. Ensure that these roles are well-defined and understood throughout the organization.
Step 4: Develop Policies and Procedures
Based on the NIST CSF guidelines and your organization’s specific needs, develop comprehensive cybersecurity policies and procedures. These documents should cover data protection, access control, network security, incident response, and more. It’s essential to align these policies with the framework’s categories and subcategories.
Step 5: Implement Security Controls
Implement security controls that align with the NIST CSF categories. These controls may include firewalls, intrusion detection systems, encryption, and access controls. Regularly update and maintain these controls to adapt to evolving threats and technologies.
Step 6: Monitor and Detect
Establish a robust monitoring and detection system to identify potential threats and vulnerabilities promptly. Implement intrusion detection systems, security information and event management (SIEM) tools, and conduct continuous security assessments. This step is crucial for the “Detect” function of the NIST CSF.
Step 7: Respond and Recover
Develop an incident response plan that outlines how your organization will react to cybersecurity incidents. Ensure that your response plan aligns with the NIST CSF’s “Respond” function. This includes roles and responsibilities during incidents, communication procedures, and recovery efforts to minimize the impact of breaches.
Step 8: Continuous Improvement
Cybersecurity is an ever-evolving field, and threats are constantly changing. Continuously review and update your governance plan and security controls to adapt to new challenges. Regularly assess your organization’s adherence to the NIST CSF and make adjustments as needed.
Step 9: Training and Awareness
Invest in cybersecurity training and awareness programs for your employees. Educated and aware staff are your first line of defense against cyber threats. Ensure that everyone in your organization understands their role in maintaining a secure environment.
Step 10: Third-Party Assessment
Consider engaging third-party cybersecurity experts to assess your organization’s adherence to the NIST CSF. An external perspective can provide valuable insights and recommendations for improvement.
Conclusion
Creating a governance plan to adhere to the NIST Cybersecurity Framework is a critical step in protecting your organization from cyber threats. By understanding the framework, assessing your current state, developing comprehensive policies, implementing security controls, and continuously improving your cybersecurity posture, you can enhance your organization’s resilience against evolving threats and ensure the security of your data and assets. Prioritizing cybersecurity is not just a necessity but a strategic advantage in today’s digital landscape.
Join NRTC, SilverSky and TrustMAPP on October 4th at 2:00 PM Eastern for the webinar Protecting Critical Infrastructure: Navigating NIST Compliance for Broadband and Electric Co-ops. This webinar will discuss cybersecurity compliance and governance strategies for the broadband and electric cooperative industry, and cover what you should be doing now.