Cybersecurity Session Outlines Requirements for Broadband Funding Programs
Randy Sukow
|
As the federal government distributes grants and other forms of funding for rural broadband projects, the program rules tend to include detailed requirements for applicants to have sound cybersecurity policies in place before receiving any support. NRTC this week hosted a webinar to help members applying for funding through the National Telecommunications and Information Administration’s (NTIA’s) Broadband Equity, Access, and Deployment (BEAD) program and the Enhanced Alternative Connect America Cost Model (Enhanced A-CAM), a component of the FCC’s universal service program.
The webinar was one of NRTC’s activities for October National Cyber Security Awareness Month.
“In the past, a lot of these cyber initiatives have been kind of reactive. You can go after funding, get the funding and then prove after the fact that you have cybersecurity in place,” said session leader Tom Neclerio, senior VP of Security Services for NRTC cybersecurity partner SilverSky. “Now with both BEAD and A -CAM they’re requiring [cybersecurity preparation] as a prerequisite before you get the funding.”
BEAD and Enhanced A-CAM rules both require cyber risk management plans, not just for the applicant’s internal operations, but also a supply chain plan. Broadband construction projects often require automated online communications between the internet provider and vendors providing materials. Cybersecurity plans must expand to meet all possible sources of danger. Both the regular and supply-chain plans must conform to the National Institute of Science and Technology (NIST) cybersecurity framework.
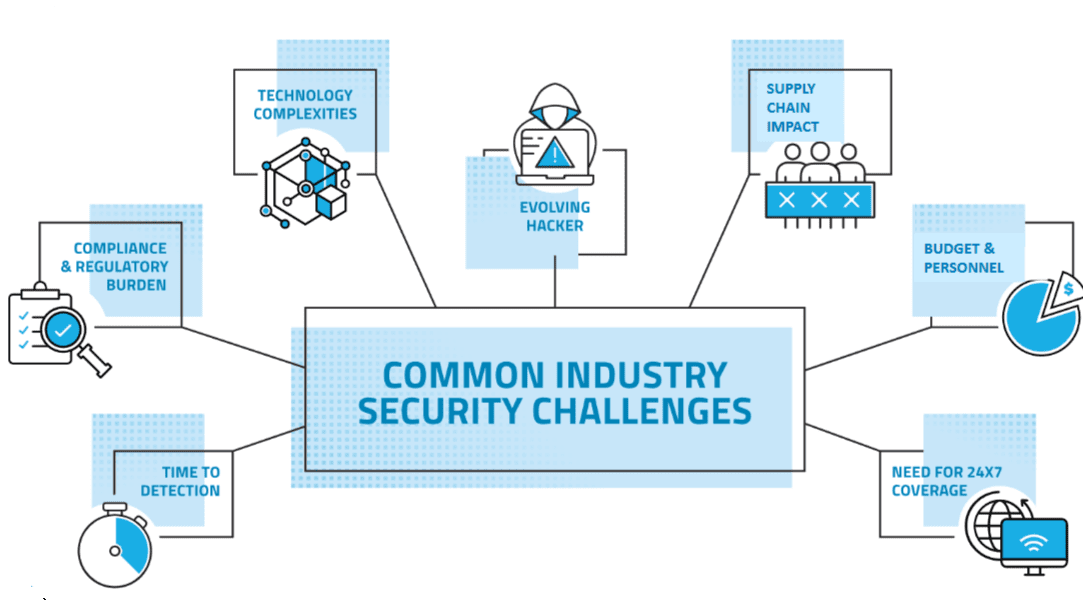
Neclerio listed several security challenges the funding program rules seek to address (see graphic above). For rural providers, he said, problems with budgeting and finding personnel to fight online attacks are especially acute. Providers rarely have dedicated staff on site. But he identified “the evolving hacker” as the most serious issue.
“It used to be the teenage hacker coming home from high school, scanning IP ranges to see what’s out there. If they hit your organization, it was just by chance,” Neclerio said. “We’ve evolved to more criminal actors out there for monetary gain, who typically are doing ransomware and things that siphon money off your accounts. And you have nation-state actors that are hitting critical infrastructure and stealing secrets.”
The webinar goes into detail on the BEAD/Enhanced A-CAM rules and what goes into building and maintaining risk management plans on a regular basis. “Security is continuous … There is no finish line in security,” he said.
A recording of the 30-minute presentation is available on NRTC’s website. For more information, contact managedservices@nrtc.coop.


